Biometric Access Control for Modern Teams
Secure - Seamless Hack-resistant
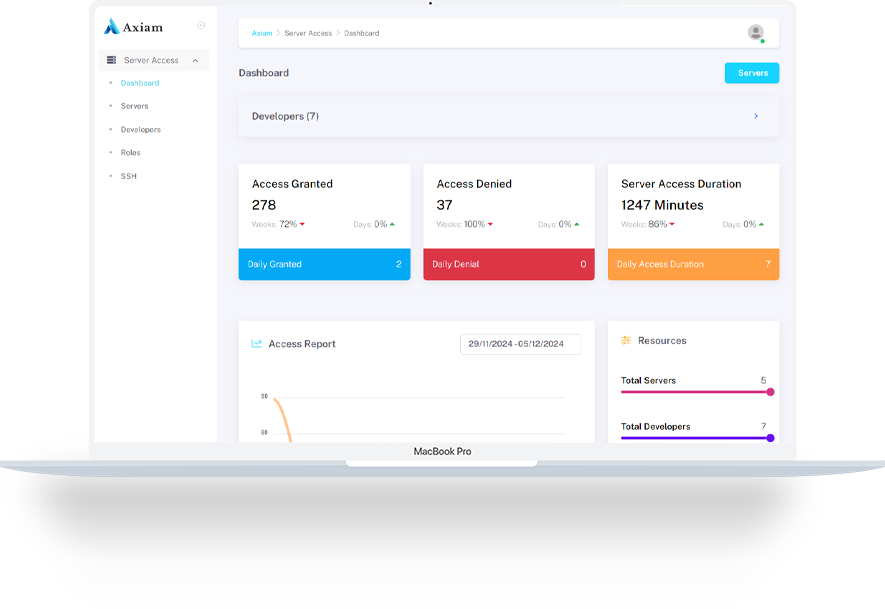
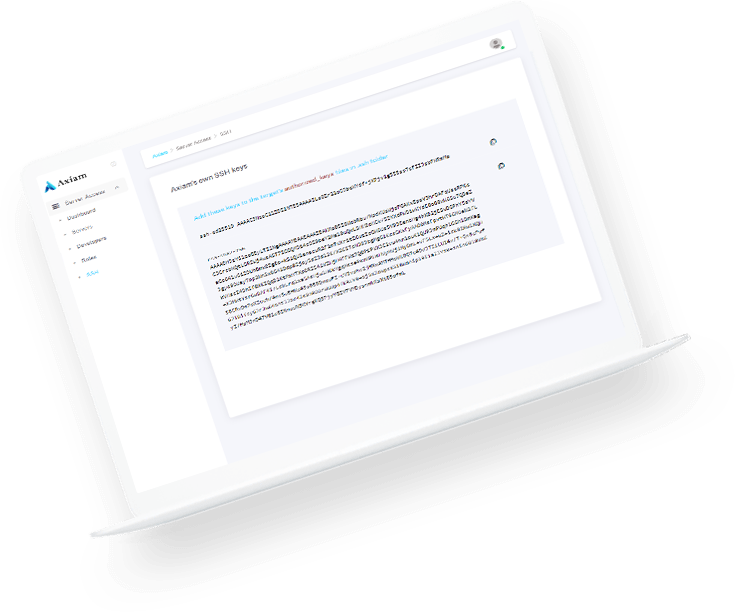
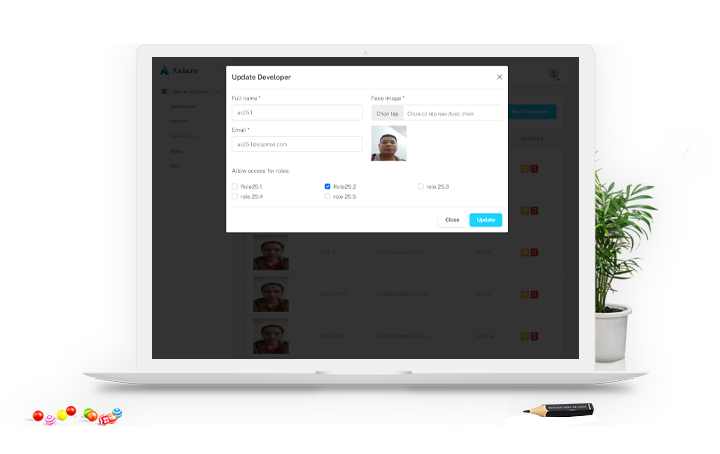
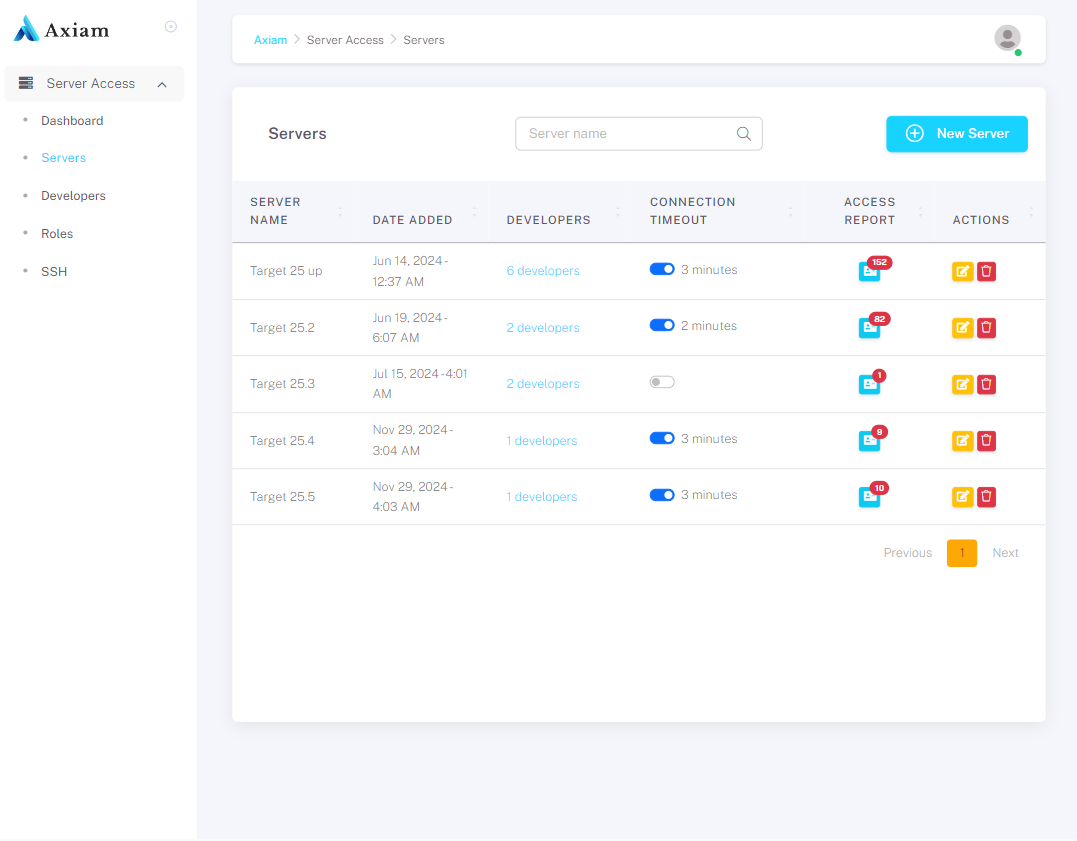
Axiam's biometric cybersecurity services deliver secure, efficient access to enterprise systems, empowering businesses to enhance operations, protect critical infrastructure, and mitigate cyber risks.